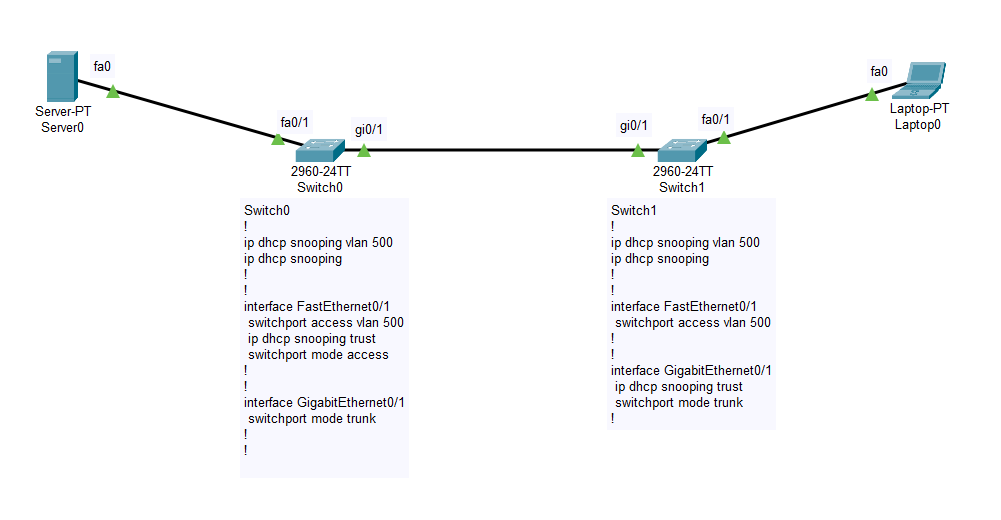
Lets look at this topology. The Server0 is configured with DHCP service and then it is connected to the Switch0 on port Fa0/1. This switch is connected to Switch1 from port Gi0/1 to Gi0/1. The laptop which is a DHCP client is connected to the Switch1 on Fa0/1.

Switch0
!
ip dhcp snooping vlan 500
ip dhcp snooping
!
!
interface FastEthernet0/1
switchport access vlan 500
ip dhcp snooping trust
switchport mode access
!
!
interface GigabitEthernet0/1
switchport mode trunk
!
!
Switch1
!
ip dhcp snooping vlan 500
ip dhcp snooping
!
!
interface FastEthernet0/1
switchport access vlan 500
!
!
interface GigabitEthernet0/1
ip dhcp snooping trust
switchport mode trunk
!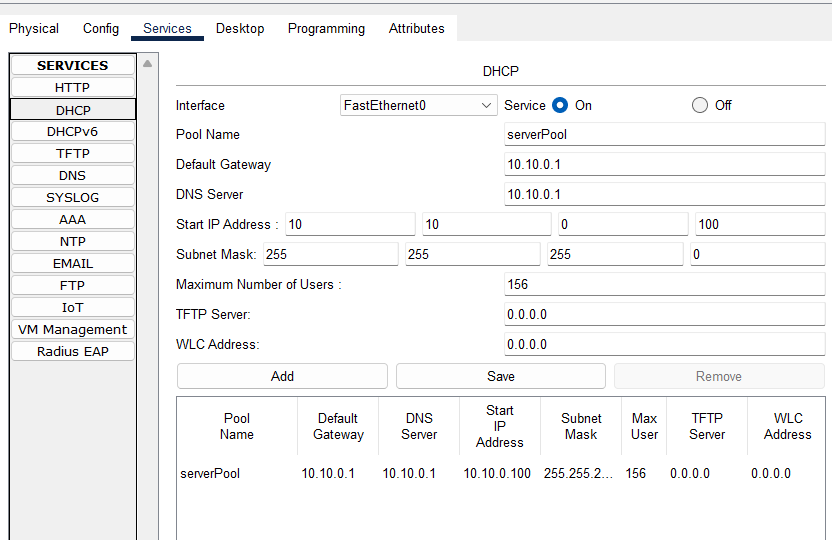

When the client is trying to get an address, it is not able to reach to the server because the cisco switches add option 82 by default to the DHCP requests and when that option is present on the packet, the other switches discard those packets with this message on the console
00:10:52: %DHCP_SNOOPING-5-DHCP_SNOOPING_NONZERO_GIADDR: DHCP_SNOOPING drop message with non-zero giaddr or option82 value on untrusted port, message type: DHCP RELEASE, MAC sa: 0005.5E80.090B
Here are three ways to fix this issue:
- Least secure which will open a security risk: To trust the Gi0/1 port on the Switch0.
Switch(config-if)#inter gi 0/1
Switch(config-if)#ip dhcp snooping trust
Switch(config-if)#
2. Somewhat better and safer: Disable the addition of option 82 on the DHCPREQUEST packets. This needs to be done on the switch where the end client is connected. In our case it is the Switch1
Switch1(config)#no ip dhcp snooping information option
Switch1(config)#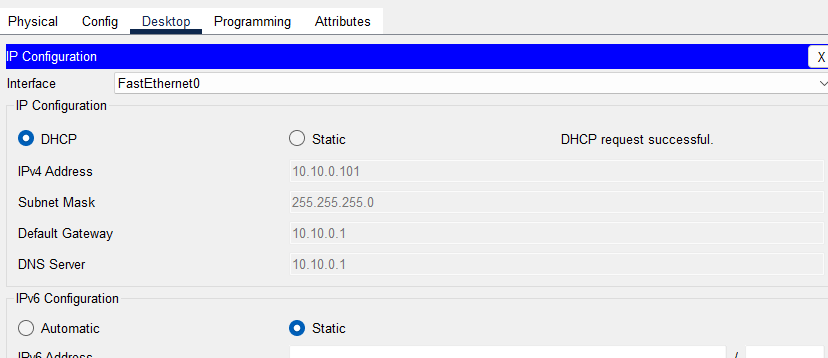
3. The best option in my understanding: To allow the packets with option 82 make it to the DHCP server. We enable it on the upstream switch to allow DHCPREQUEST packets coming from untrusted ports. In our case we enable it on the Switch0
Switch0(config)#
Switch0(config)#ip dhcp snooping information option allow-untrusted
Switch0(config)#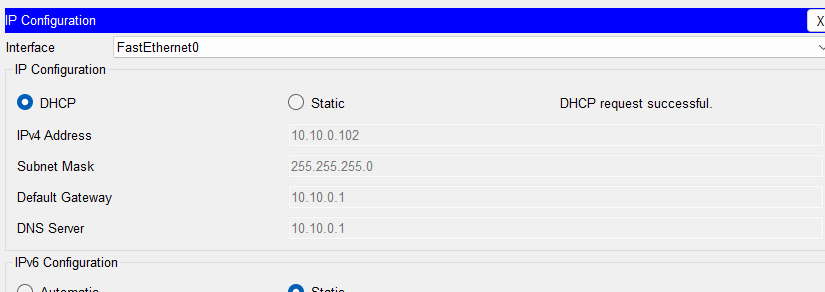
I have attached the Cisco Packet Tracer file here. You can download the .pkt file for your tinkering pleasure.
