Category: Tutorial
DHCP snooping not working – multiple switches in path
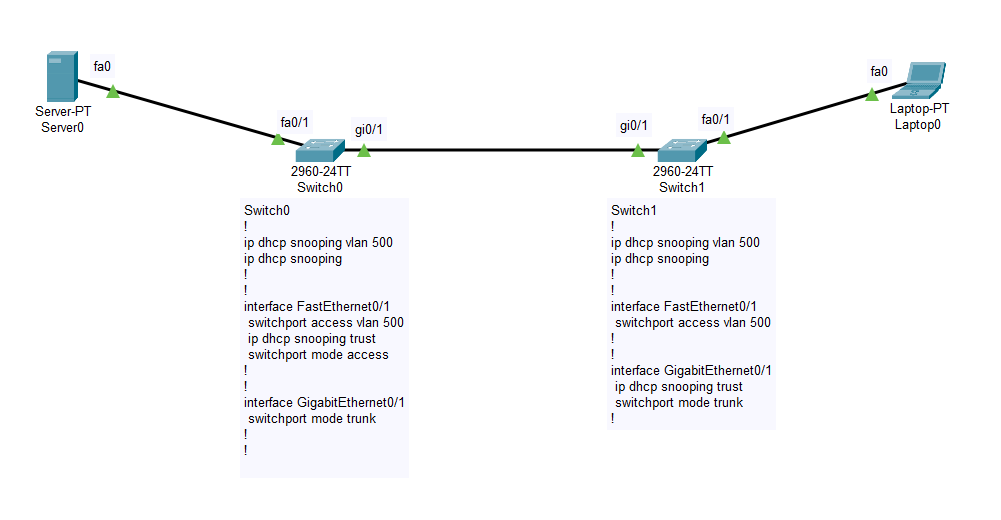
Lets look at this topology. The Server0 is configured with DHCP service and then it is connected to the Switch0 on port Fa0/1. This switch…
How utilize SSH tunnel for any remote service
This is something Advanced level so if you are a beginner, try to follow along and I will try to explain it in the easiest…
[How To] Create Bootable Windows XP USB
Yesterday I ran into trouble while trying to install Windows XP on an old computer. The problem? Well I didn’t have a CD ROM drive…
